Security for near field communication systems in e-payment application
Overview of near field communication system
Near Field Communication (NFC) is a technology for short-distance, wireless,
high-frequency point-to-point communications. The operating range of NFC is
within 20 cm [3], which is good from a security perspective as it reduces the risk
of eavesdropping. Other reasons to use NFC are the low cost of the required
components and the connection time is negligible. It is a small circuit attached to a
small antenna, capable of transmitting data up to several meters to a reading device
(reader) in response to the query.
The world NFC market is predicted to generate $ 24 billion in revenue by 2020
[1]. North America dominates the world NFC market, due to the strong demand
from the US, but the trend shows the Asia-Pacific region will have a faster growth
rate in the next period1.
Key companies currently doing research and development in this area include
Infineon Technologies, Apple Inc., NXP, Samsung Electronics Co. Ltd., Broadcom
Corporation, Toshiba Corporation, and Inside Secure - now acquired by Intel [14].
In this paper, we focus on the product lines from NXP, considering this is the
most representative NFC devices and NXP currently is the biggest NFC supplier
worldwide1. Particularly, the most representative product lines of the company
today, NFC EV2 smart card and MCU PN7462AU integrated front-end MCU for
the smart card reader [2].

Trang 1

Trang 2

Trang 3

Trang 4
Trang 5

Trang 6
Trang 7
Trang 8

Trang 9

Trang 10
Tóm tắt nội dung tài liệu: Security for near field communication systems in e-payment application

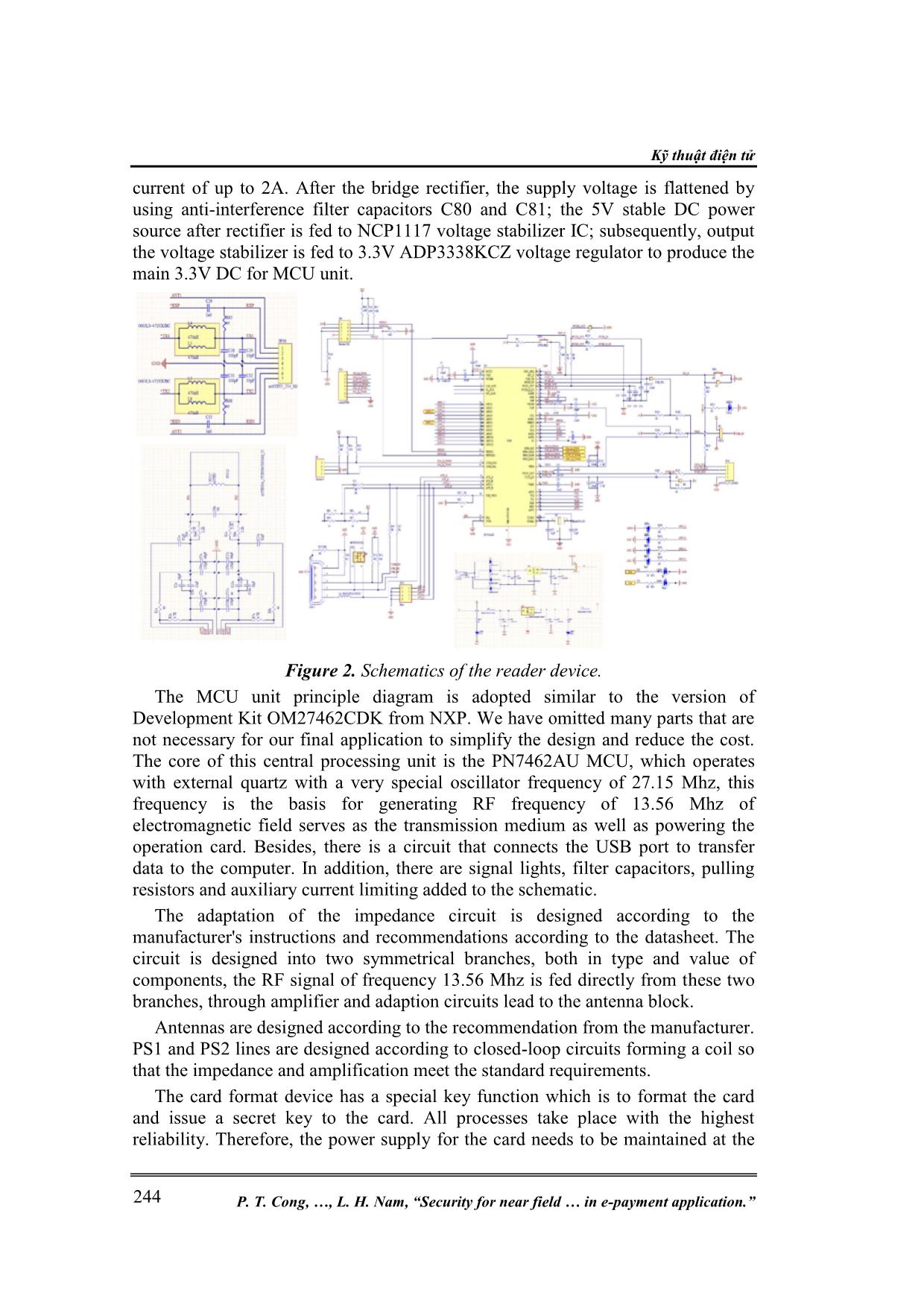
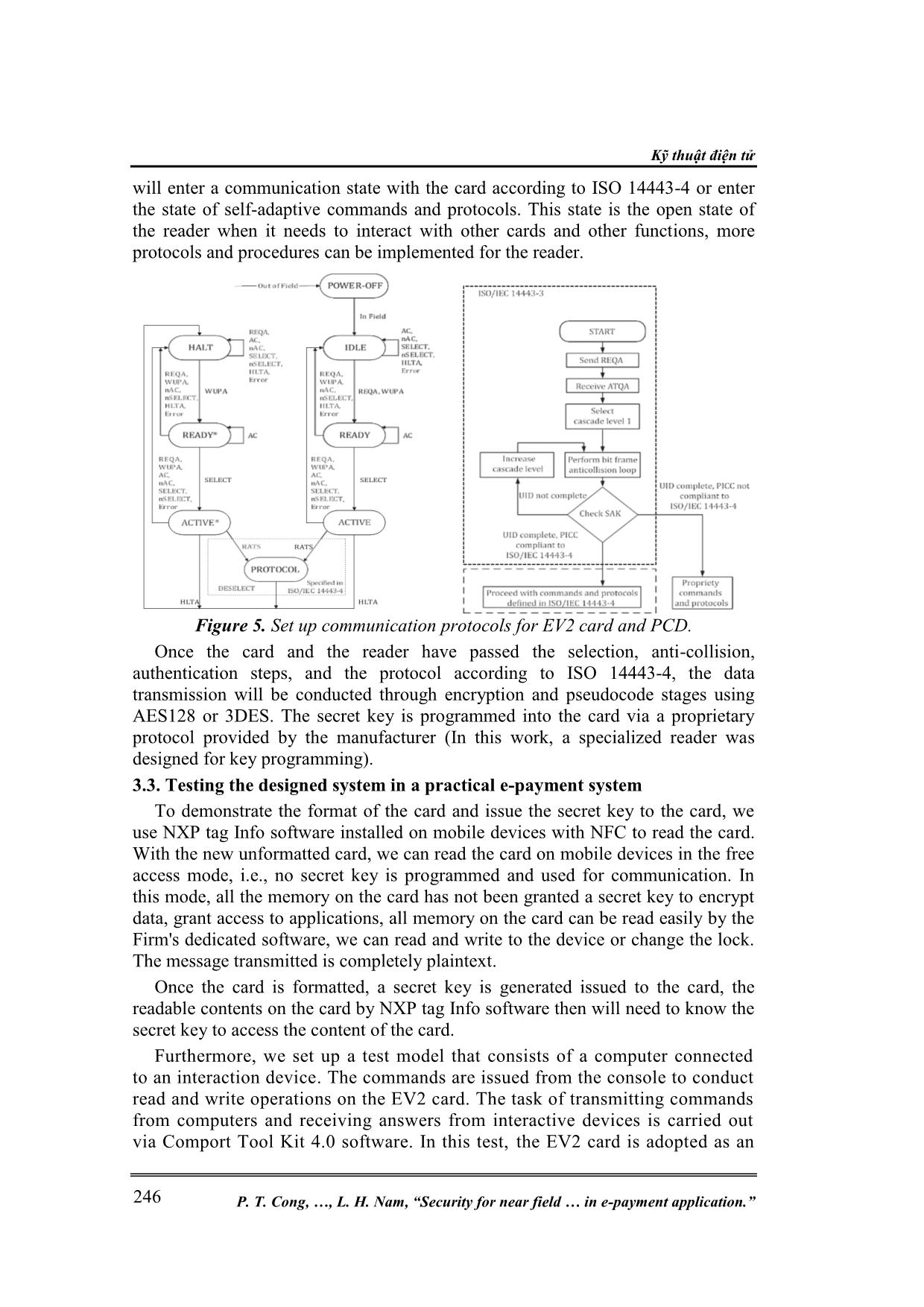
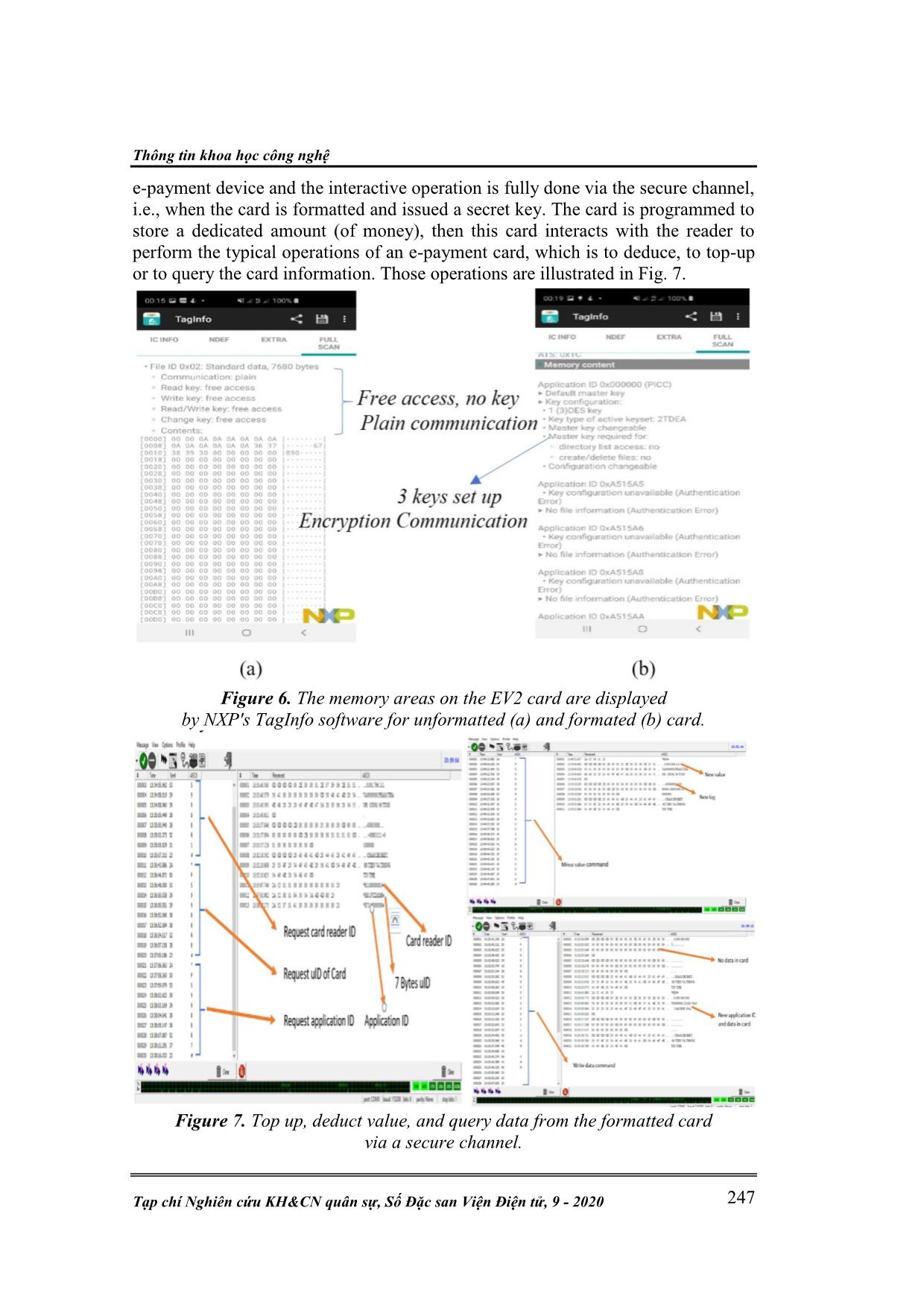
Kỹ thuật điện tử P. T. Cong, , L. H. Nam, “Security for near field in e-payment application.” 240 SECURITY FOR NEAR FIELD COMMUNICATION SYSTEMS IN E-PAYMENT APPLICATION Pham Thanh Cong 1* , Trinh Quang Kien 2 , Nguyen Ngoc Thai 1 , Le Hai Nam 2 Abstract: The paper presents an overview of the near field communication system NFC, current trends, and application status of the system. The paper points out the security risks of the system involving both intentional and unintentional attacks [3]. In the next section, the paper presents measures to prevent the indicated security risks. Finally, we suggest a total solution based on the design and creation of a complete NFC system for one of the applications that need the highest security- payment via smart card on the latest components in the NFC field of NXP. Keywords: NFC; E-payment; Mifare DESfire; EV2; RF; Hardware security; Digital channel. 1. OVERVIEW AND SECURITY ISSUES OF NEAR FIELD COMMUNICATION SYSTEMS 1.1. Overview of near field communication system Near Field Communication (NFC) is a technology for short-distance, wireless, high-frequency point-to-point communications. The operating range of NFC is within 20 cm [3], which is good from a security perspective as it reduces the risk of eavesdropping. Other reasons to use NFC are the low cost of the required components and the connection time is negligible. It is a small circuit attached to a small antenna, capable of transmitting data up to several meters to a reading device (reader) in response to the query. The world NFC market is predicted to generate $ 24 billion in revenue by 2020 [1]. North America dominates the world NFC market, due to the strong demand from the US, but the trend shows the Asia-Pacific region will have a faster growth rate in the next period 1 . Key companies currently doing research and development in this area include Infineon Technologies, Apple Inc., NXP, Samsung Electronics Co. Ltd., Broadcom Corporation, Toshiba Corporation, and Inside Secure - now acquired by Intel [14]. In this paper, we focus on the product lines from NXP, considering this is the most representative NFC devices and NXP currently is the biggest NFC supplier worldwide1. Particularly, the most representative product lines of the company today, NFC EV2 smart card and MCU PN7462AU integrated front-end MCU for the smart card reader [2]. A basic NFC system consists of two main components: The reader and the tags or interacting device, which is an object with an embedded NFC chip, the latter can be either a standalone smart card or mobile phone, camera, or other objects with embedded NFC chip. For complex systems, additional components may exist such as computers, networks, servers, additional security components such as biometric security: fingerprint sensor, face recognition camera, and other executive components, services such as opening and closing, ATM, cumulative counter, etc. 1 Most NFC chips, NFC tags are now manufactured by NXP, while others have a small market share (According to www.grandviewresearch.com). Thông tin khoa học công nghệ Tạp chí Nghiên cứu KH&CN quân sự, Số Đặc san Viện Điện tử, 9 - 2020 241 Figure 1. Components of the NFC system and interactive operation of NFC. The analysis in [1] indicates that most NFC tags are passive, meaning they are battery-free and get power from the query signal. They can be attached to almost everything: goods, clothing, food, access cards, etc. Up to date, there are three typical applications of NFC technology which are subsequently discussed in the following: Wireless token, pair devices, e-ticket, e-payment, etc. When tags and devices with NFC chips are put into the interaction distance of the RF field created by the NFC reader, the processes take place as follows: the card receives energy from the RF signal through electromagnetic induction from its integrated antenna, accumulates through the circuit to create a stable power source for the chip in the card to start working. The interactive device generates synchronous pulses as well as initiates a question-and-answer process to authenticate the protocol, access rights of the card, secret keys for code, and pseudo-transmitting information. 1.2. Security in the NFC system Since NFC is a wireless communication interface, there are inevitable security threats associated with the transmission medium and its transmitted data. When two devices communicate via NFC, they use RF waves to talk to each other. An attacker could easily catch the transmitted data via the RF interface and with sufficient samples or when the data is not encrypted, the attacker can gain the necessary knowledge about the actual contents. This can be done without any special equipment and potentially lead to severe consequences in some critical applications such as e-banking, e-payment, and/or militar ... ore, be preferred. NFC device can check the RF field during sending. This means that the sending device can continually check for such an attack and may stop transmitting data when an attack is detected. The third and perhaps best solution would be a secure channel as described in section 3. Thông tin khoa học công nghệ Tạp chí Nghiên cứu KH&CN quân sự, Số Đặc san Viện Điện tử, 9 - 2020 243 Anti data insertion There are three possible countermeasures to insertion attacks. First, the card performs the answering device without delay. In this case, the attacker cannot be faster than the correct device. The controller may be as fast as the correct device, but if two devices reply at the same time, they will not receive the correct data. The second countermeasure might be listening by the channel answering device during that time, it opens and the starting point of the line. The device can then detect an attacker who wants to insert data. And the third option is to establish a secure channel between the two devices. Anti Man in the Middle attack As stated in the section above, it is practically impossible to carry out an intermediary attack on the NFC link. It is recommended to use the active-passive communication mode so that the RF field is continuously generated by one of the valid parties. Also, the operator should listen for RF submissions while sending data so that it can detect any disturbance caused by an attacker likely to cause it. 3. DESIGN A HIGH-SECURITY NFC SYSTEM AND THE EXPERIMENTAL MODEL FOR E-PAYMENT This section proposes a total solution to build an NFC system with the up-to- dated security features based on the latest technologies of NXP with Mifare Desfire EV2 and PN7462 chips. The design of a complete NFC system, including the hardware and software modules, have been presented. The design strictly follows the technical standards and requirements from the manufacturer, especially for the security aspects. The data exchange between the card readers and cards is fully encrypted by using either AES-128 or 3-DES. The secret key is negotiated and shared via a private and proprietary channel. The system has been fully implemented and tested. The practical test results indicate that the designed system meets the basic features for an NFC card payment service and is ready for real applications. 3.1. Design specialized NFC interactive equipment and specialized proximity coupling device In this work, we have developed to make two types of interactive devices. One is the card formatted, that performs card format, that including setting up secret key for the card via a proprietary interface (i.e., accessible by NXP proprietary devices only). The other is the card reader performs all basic interactions with the card such as: read the contents of the card, top-up and deduct the value of the card, record the card's ID, and interact with the computer to receive orders and respond to the status. These two interactive devices have the same hardware principle diagram, the difference here is that the latter is equipped additional display section for users to easily observe and track the interaction process of the card. The power of the system uses two main voltages: 3.3V and 5V, the power supply for the system is designed to input a wide voltage range but does not need to be high stability. The main solution consists of an AC bridge implemented on four Schottky PMEG302EJ diodes with a withstand voltage of up to 30V and a Kỹ thuật điện tử P. T. Cong, , L. H. Nam, “Security for near field in e-payment application.” 244 current of up to 2A. After the bridge rectifier, the supply voltage is flattened by using anti-interference filter capacitors C80 and C81; the 5V stable DC power source after rectifier is fed to NCP1117 voltage stabilizer IC; subsequently, output the voltage stabilizer is fed to 3.3V ADP3338KCZ voltage regulator to produce the main 3.3V DC for MCU unit. Figure 2. Schematics of the reader device. The MCU unit principle diagram is adopted similar to the version of Development Kit OM27462CDK from NXP. We have omitted many parts that are not necessary for our final application to simplify the design and reduce the cost. The core of this central processing unit is the PN7462AU MCU, which operates with external quartz with a very special oscillator frequency of 27.15 Mhz, this frequency is the basis for generating RF frequency of 13.56 Mhz of electromagnetic field serves as the transmission medium as well as powering the operation card. Besides, there is a circuit that connects the USB port to transfer data to the computer. In addition, there are signal lights, filter capacitors, pulling resistors and auxiliary current limiting added to the schematic. The adaptation of the impedance circuit is designed according to the manufacturer's instructions and recommendations according to the datasheet. The circuit is designed into two symmetrical branches, both in type and value of components, the RF signal of frequency 13.56 Mhz is fed directly from these two branches, through amplifier and adaption circuits lead to the antenna block. Antennas are designed according to the recommendation from the manufacturer. PS1 and PS2 lines are designed according to closed-loop circuits forming a coil so that the impedance and amplification meet the standard requirements. The card format device has a special key function which is to format the card and issue a secret key to the card. All processes take place with the highest reliability. Therefore, the power supply for the card needs to be maintained at the Thông tin khoa học công nghệ Tạp chí Nghiên cứu KH&CN quân sự, Số Đặc san Viện Điện tử, 9 - 2020 245 most stable level so that during the process of formatting and transmitting the secret key and the antenna is designed with a sufficiently large size. Figure 3. PCB of card format device and PCD. Figure 4. The shape and layout of the card format device and PCD. Specialized PCD is designed with a compact shape that is convenient to deploy in public service areas, so in the design, it integrates both central processing unit and antenna on one board with compact size. The PCB designs and the final prototypes are shown in Fig. 4. 3.2. Communication protocols setting for card and reader According to the datasheet of the EV2 card, the algorithm flowchart of the card's protocol with the reader is shown in figure 5. From the figure, when the card is outside the interactive field, it will be off, when entering the interactive field, the induction circuits accumulate energy and the card becomes activate and start listening. After that, the card is ready for issuing commands AC, nAC, SELECT, nSELECT, HLTA, error, REQA, WUPA to get ready. When ready, if the tag receives a SELECT statement, the tag enters the active state; In other cases, the card will return to the listening state. In the active mode, the card will wait for media protocol confirmation, if the card and the reader agree on the communication protocol standard, the data transmission can be started. From there, the flowchart of the algorithm for setting the protocol for the EV2 card reader can be constructed as follow. Initially, the reader sent the REQA command, waiting for the ATQA command response from the card (structure these commands according to the standard ISO 14443). Next comes the anti-conflict loop as described above. By checking the SAK from the feedback card, the reader Kỹ thuật điện tử P. T. Cong, , L. H. Nam, “Security for near field in e-payment application.” 246 will enter a communication state with the card according to ISO 14443-4 or enter the state of self-adaptive commands and protocols. This state is the open state of the reader when it needs to interact with other cards and other functions, more protocols and procedures can be implemented for the reader. Figure 5. Set up communication protocols for EV2 card and PCD. Once the card and the reader have passed the selection, anti-collision, authentication steps, and the protocol according to ISO 14443-4, the data transmission will be conducted through encryption and pseudocode stages using AES128 or 3DES. The secret key is programmed into the card via a proprietary protocol provided by the manufacturer (In this work, a specialized reader was designed for key programming). 3.3. Testing the designed system in a practical e-payment system To demonstrate the format of the card and issue the secret key to the card, we use NXP tag Info software installed on mobile devices with NFC to read the card. With the new unformatted card, we can read the card on mobile devices in the free access mode, i.e., no secret key is programmed and used for communication. In this mode, all the memory on the card has not been granted a secret key to encrypt data, grant access to applications, all memory on the card can be read easily by the Firm's dedicated software, we can read and write to the device or change the lock. The message transmitted is completely plaintext. Once the card is formatted, a secret key is generated issued to the card, the readable contents on the card by NXP tag Info software then will need to know the secret key to access the content of the card. Furthermore, we set up a test model that consists of a computer connected to an interaction device. The commands are issued from the console to conduct read and write operations on the EV2 card. The task of transmitting commands from computers and receiving answers from interactive devices is carried out via Comport Tool Kit 4.0 software. In this test, the EV2 card is adopted as an Thông tin khoa học công nghệ Tạp chí Nghiên cứu KH&CN quân sự, Số Đặc san Viện Điện tử, 9 - 2020 247 e-payment device and the interactive operation is fully done via the secure channel, i.e., when the card is formatted and issued a secret key. The card is programmed to store a dedicated amount (of money), then this card interacts with the reader to perform the typical operations of an e-payment card, which is to deduce, to top-up or to query the card information. Those operations are illustrated in Fig. 7. Figure 6. The memory areas on the EV2 card are displayed by NXP's TagInfo software for unformatted (a) and formated (b) card. Figure 7. Top up, deduct value, and query data from the formatted card via a secure channel. Kỹ thuật điện tử P. T. Cong, , L. H. Nam, “Security for near field in e-payment application.” 248 4. CONCLUSIONS This paper has conducted a comprehensive study on the NFC system and application, which specially focuses on the security aspects. First, the fundamental background and basic concepts of NFC systems have been presented. The security issues in NFC systems, which are the main focus of this paper then have been discussed. A throughout survey on theoretical and practical security breaches of the NFC has been given that concludes that the security threat is serious and it could have a strong impact on the development and application of NFC. Therefore, it is essential to have enhanced technology for securing the NFC system. The remaining of the paper presented a practical solution from NXP to tackle the security issue in the next generation of NXP devices and systems. This solution has been fully deployed as a complete system, including hardware and software modules for programming the cards and these interactions. The practical verification result of the deployed system showed that the proposed solution meets most of the basic requirements. As the major technical enhancement, the communication channel is encrypted by using adequate ciphers (AES or TDES), where the key exchange is conducted through a proprietary tool and device. The testing scenarios for the system is built based on the real e-payment application. The major testing results indicate that the system can successfully perform secure transactions and is ready for the actual application. REFERENCES [1]. M. M. A. Allah, "Strengths and Weaknesses of Near Field Communication (NFC) Technology," Global Journal of Computer Science and Technology, p. 7, 2011. [2]. S. D. Dominic Schurmann, "OpenKeychain: An Architecture for Cryptography with Smart Cards and NFC Rings on Android," LARS WOLF, Vols. Vol. 1, No. 3,Article99, no. Proceedings of the ACM on Interactive, Mobile, Wearable and Ubiquitous Technologies, p. 24, 2017. [3]. S. Jasek, “A 2018 practical guide to hacking NFC/RFID”, Kraków: Confidence, 2018. [4]. R. Meindl, “NFCIP-1 Security Standard Protects Near Field Communication”, Sophia Antipolis: ETSI Security Workshop, 2009. [5]. NXP, “MIFARE product and handling of UIDs AN10927”, Eindhoven, Netherlands: NXP.com, 2019. [6]. R. T. Tarang, "A Literature Survey on Near Field Communication," American International Journal of Research in Science, Technology, Engineering & Mathematics, p. 9, 2017. [7]. Y. W. W. C. Jie Ling, "An Improved Privacy Protection Security Protocol Based on NFC," International Journal of Network Security, vol. 19, pp. 39-46, 2017. [8]. K. L. M. S. T. S. L. Z. Dennis Giese, “Security Analysis of Near-Field Communication (NFC) Payments”, 2018. [9]. "https://www.grandviewresearch.com/press-release/global near field communication nfc market," Grand View Research, Inc, October 2016. [Online]. [Accessed 19 April 2020]. Thông tin khoa học công nghệ Tạp chí Nghiên cứu KH&CN quân sự, Số Đặc san Viện Điện tử, 9 - 2020 249 TÓM TẮT BẢO MẬT CHO HỆ THỐNG THÔNG TIN TRƯỜNG GẦN (NFC) TRONG ỨNG DỤNG THANH TOÁN ĐIỆN TỬ Bài báo trình bày kết quả nghiên cứu về an ninh cho hệ thống thông tin trường gần gồm một số nội dung: Tổng quan và thực trạng phát triển của các hệ thống thông tin trường gần NFC; Thành phần của các hệ thống thông tin trường gần; ứng dụng và tương lai phát triển của hệ thống NFC trong thực tế; những nguy cơ và giải pháp an ninh bảo mật cho hệ thống NFC; cập nhật những hoạt động của hacker trên thế giới cũng như giải pháp mới nhất của hãng NXP trong lĩnh vực NFC; ứng dụng những giải pháp công nghệ mới của NXP để xây dựng hệ thống thực nghiệm; thử nghiệm và phát triển ứng dụng thanh toán điện tử. Nội dung nghiên cứu trình bày trong bài báo là kết quả của sự tổng hợp, nghiên cứu từ nhiều nguồn tài liệu, các bài báo khoa học khác nhau để đưa ra những nội dung tổng quát, chi tiết nhất về vấn đề nghiên cứu. Từ khóa: NFC; Thanh toán điện tử; Mifare DESfire; EV2; Bảo mật. Received 6 th April 2020 Revised 21 th August 2020 Published 28 th August 2020 Địa chỉ: 1Viện Điện tử, Viện Khoa học và Công nghệ quân sự. 2Học viện Kỹ thuật quân sự. *Email: thanhcongvdt@gmail.com.
File đính kèm:
 security_for_near_field_communication_systems_in_e_payment_a.pdf
security_for_near_field_communication_systems_in_e_payment_a.pdf

